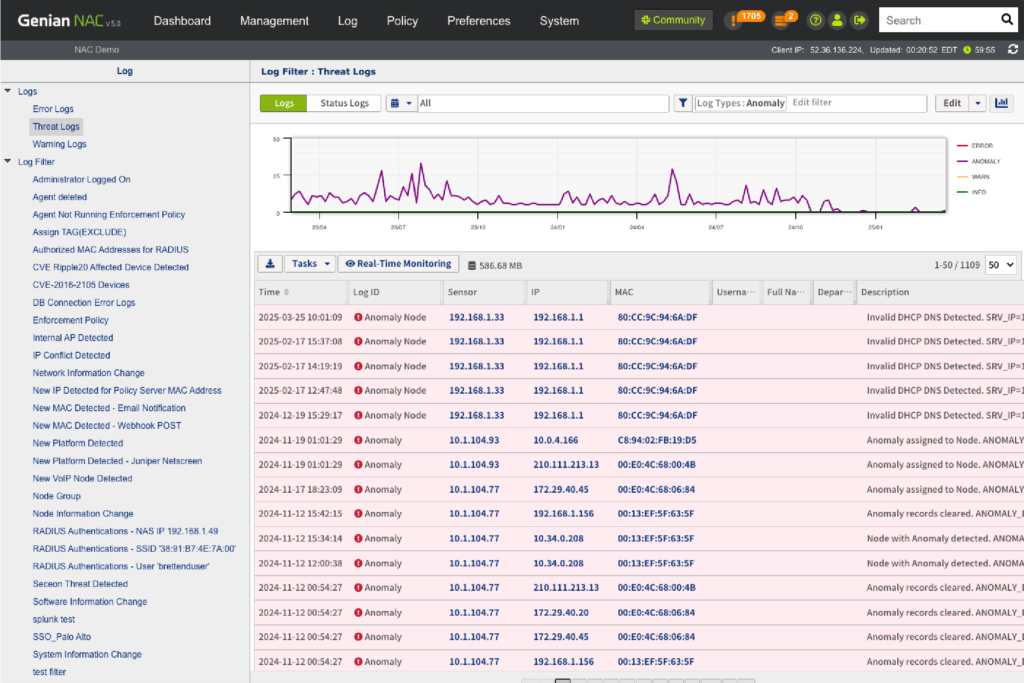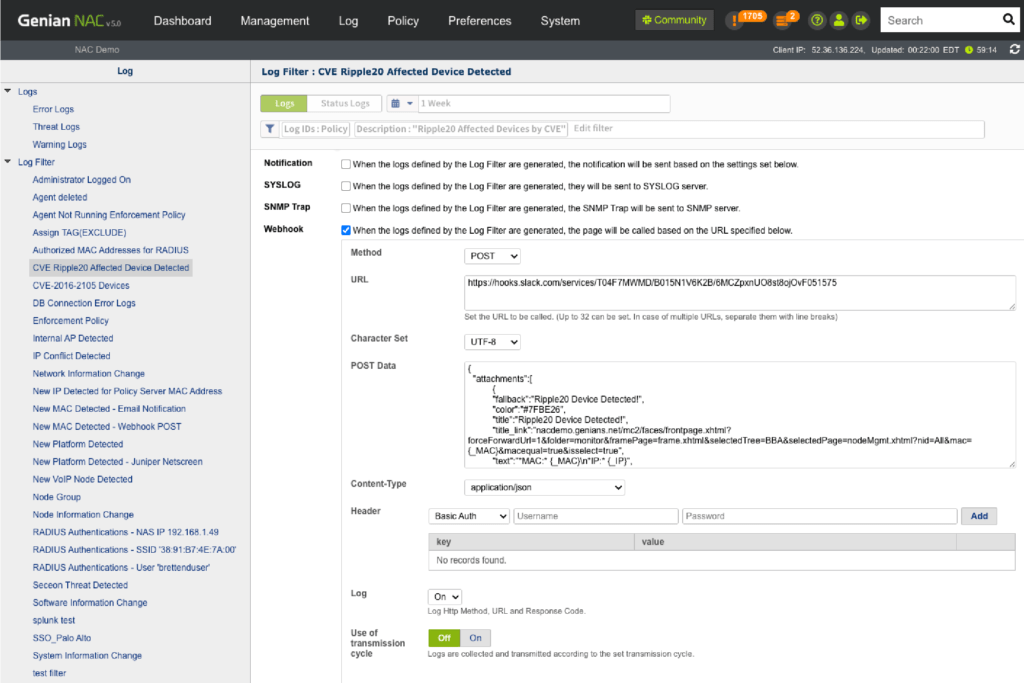
Network Access Control
AT THE FIRST CONNECTION
Genian NAC. Where Execution Begins.
WHEN A DEVICE CONNECTS
Access Decisions Enforced Before Risk Enters
When a device attempts to connect, security cannot wait for manual review or downstream response. Genian NAC enforces access decisions in real time, evaluating device identity, posture, and access context before allowing network participation. This ensures that only compliant and trusted devices become part of your operational environment.
- Identify devices and access context at the moment of connection
- Enforce access based on security posture and policy
- Block, isolate, or remediate before network exposure
Features
Execution Built Into Every Connection
Genian NAC brings enforcement to the edge of your network, applying security decisions consistently at the moment of connection through non-disruptive sensing and access control. Without requiring network changes or operational interruption, these capabilities support real-time identification, policy enforcement, and response, enabling organizations to translate security intent into reliable operational control.
Network Monitoring
Network Surveillance
Monitor any IP-enabled devices
Learn More
Device Risk Analysis
Device Platform Intelligence (DPI)
Technology + Business + Risk
Learn More
Network Surveillance
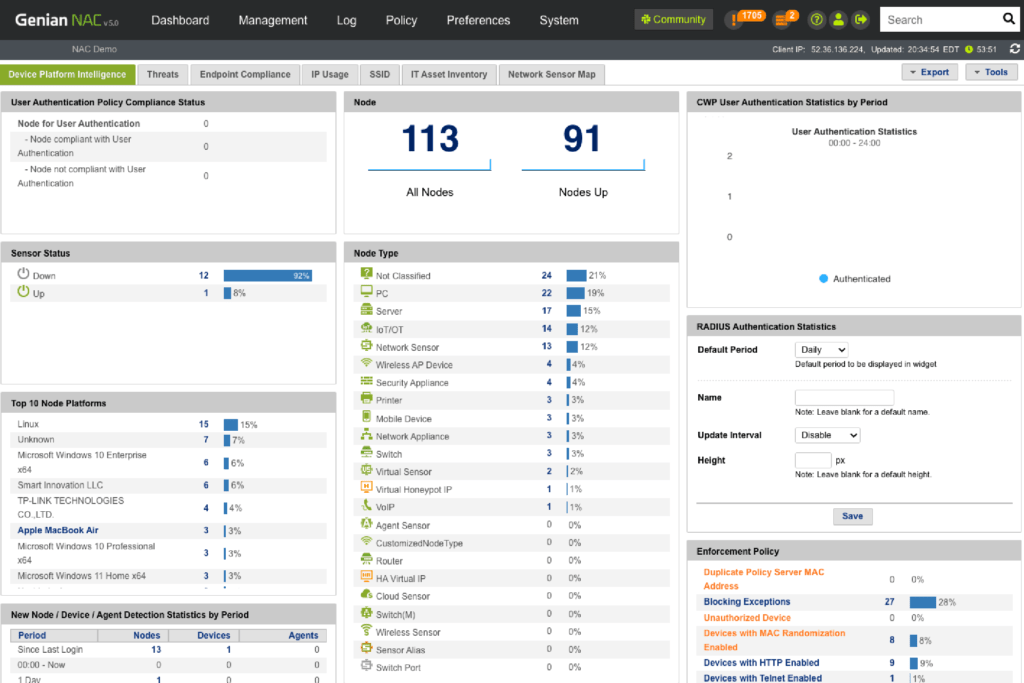
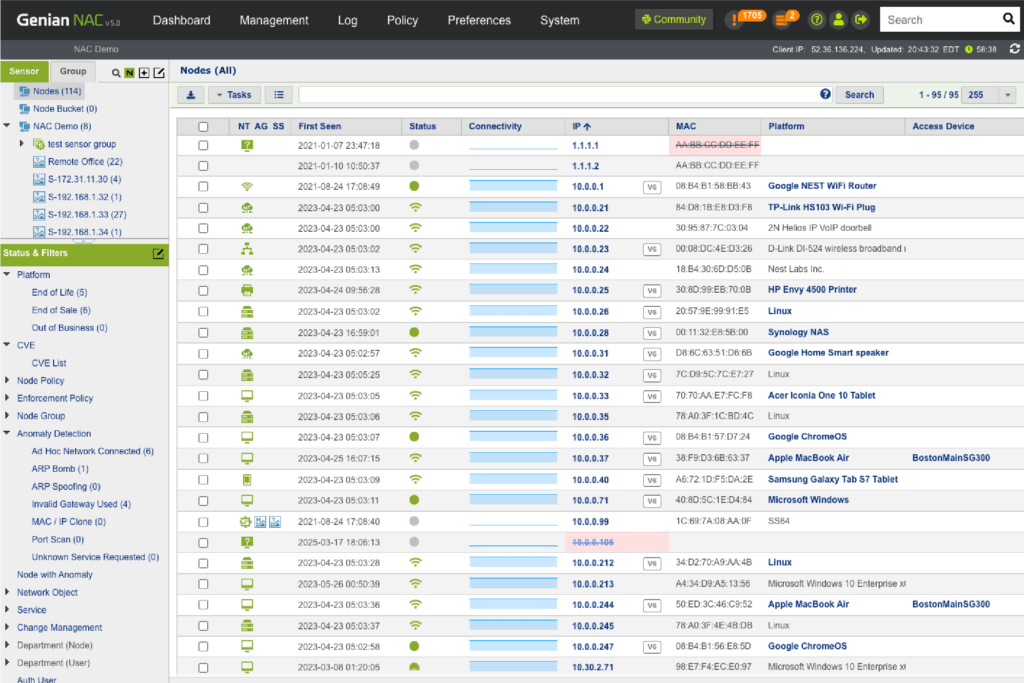
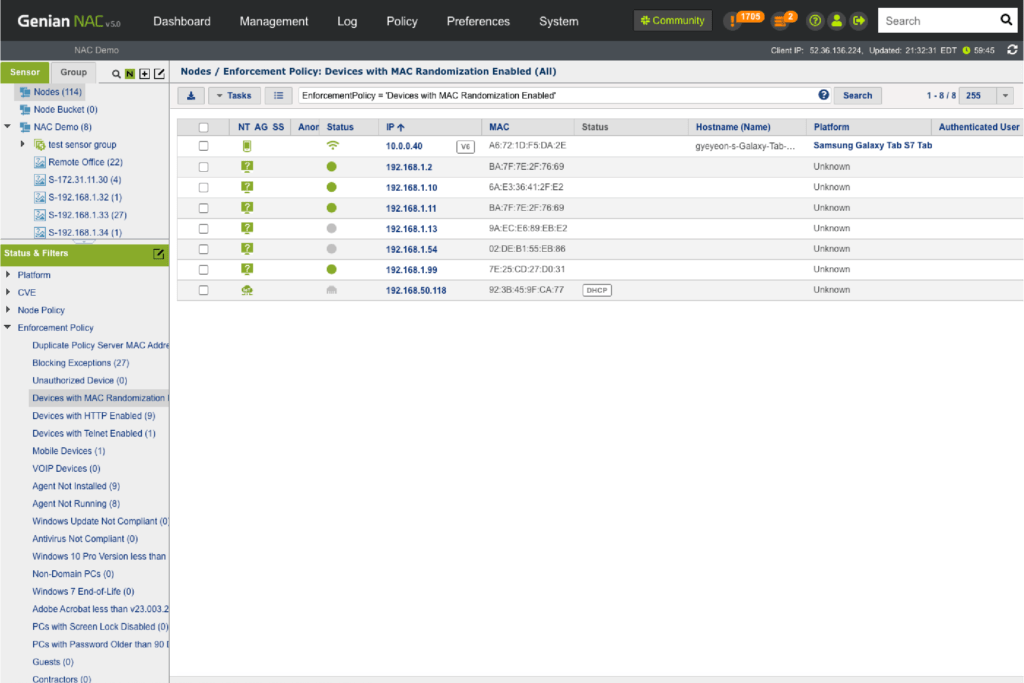
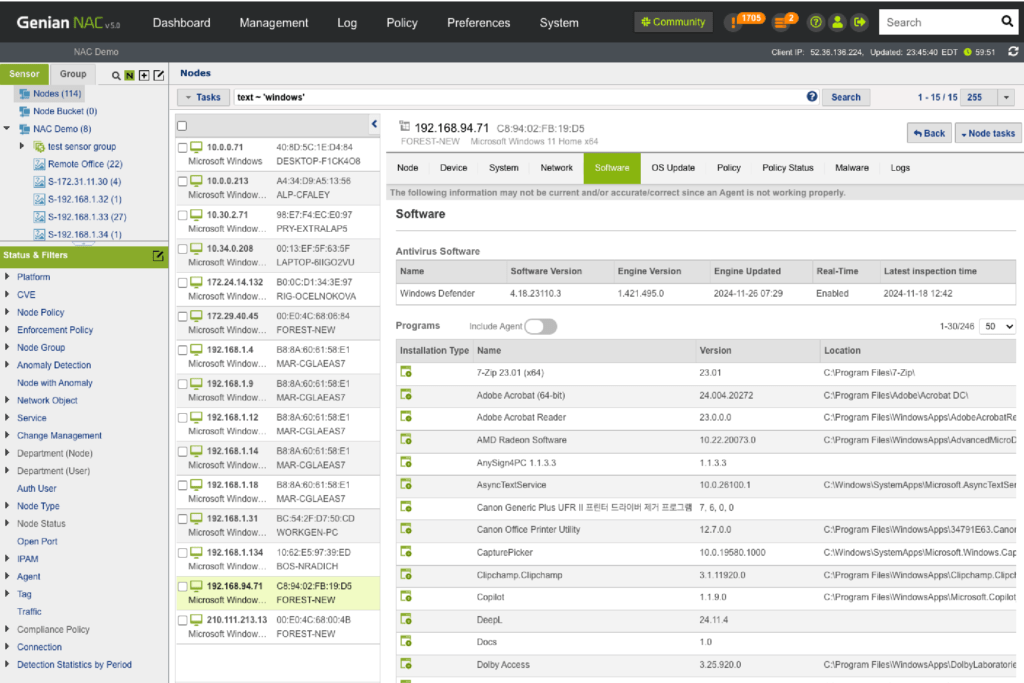
Genian NAC can monitor IP-enabled devices on your network in real-time using a non-disruptive Layer 2 based Network Sensor and classifies those devices and their users into logical groups based on your business requirements. Genian NAC has the intelligence to sort out a wide range of network-connected devices and their states to present immediate, meaningful, and actionable information.
Detection
- Provide the most accurate device platform information and see access trends
- Discover contextual access information (Who, What, Where, When, How)
- Detect compliance status change on time
Coverage
- Monitor heterogeneous network environments without changing existing network configuration
- Monitor wireless packets by Wireless Sensors or Agents
- Monitor all managed, unmanaged, and even legacy networking devices
Observation
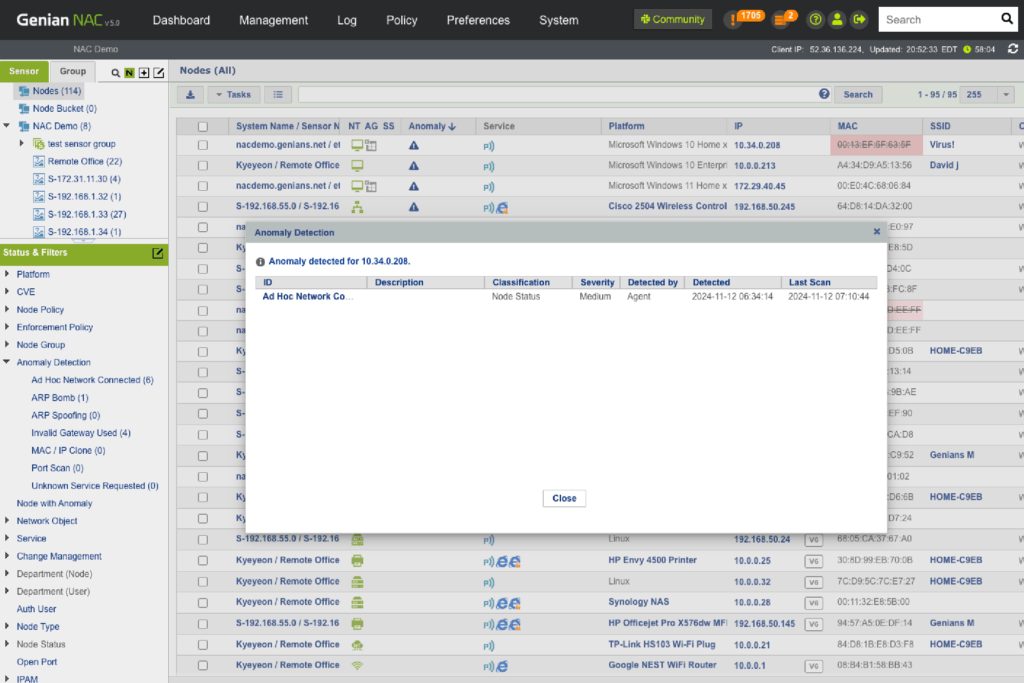
- Find non-compliant, unknown, rogue, misconfigured devices
- Discover abnormal network traffics (e.g. ARP Spoofing/Bombing, MAC/IP Cloning, Port scanning, Invalid Gateway)
- Present personalized information through fully customizable dashboards
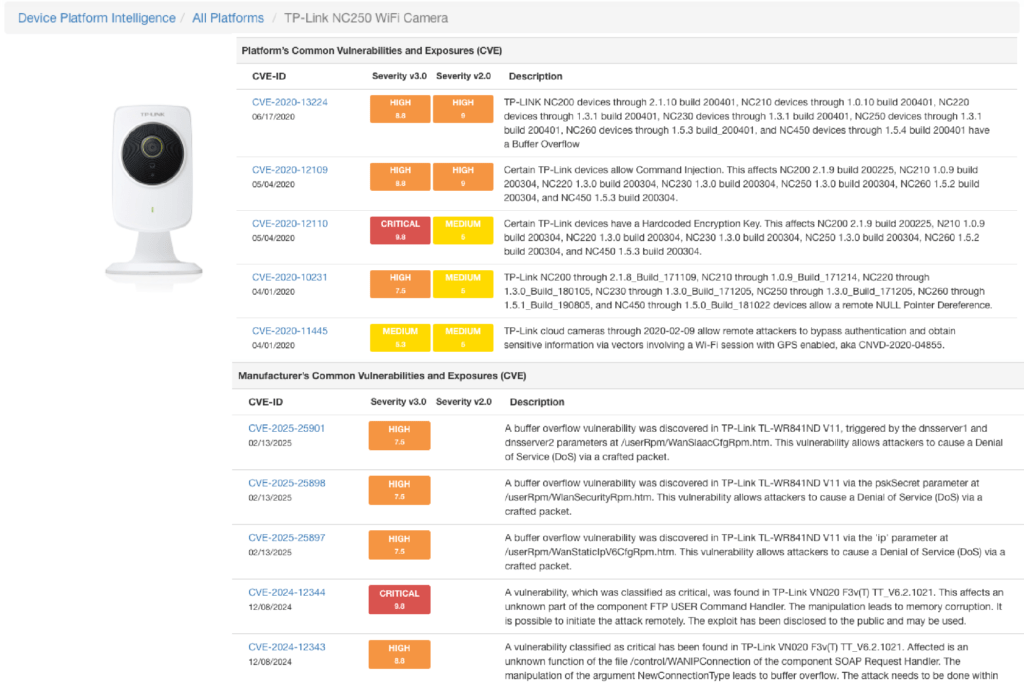
Device Platform Intelligence
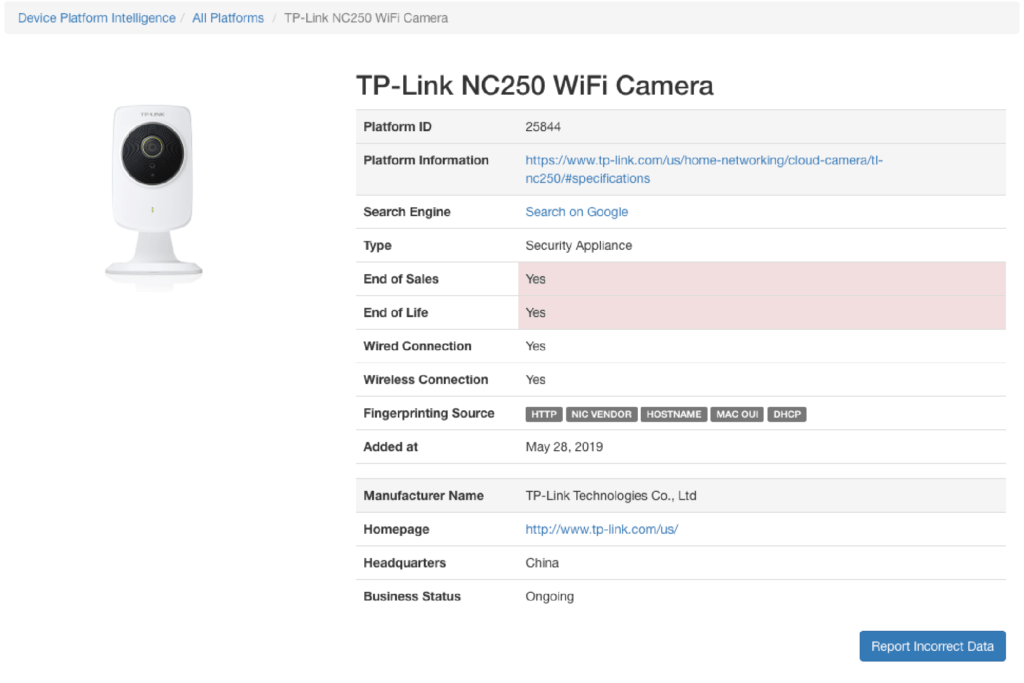
“Device Platform” refers to any hardware or software, or any combination of hardware and software (OS), used to access a network. Genian NAC incorporated with Device Platform Intelligence (DPI) can present the most accurate device identity, its contextual, and its risk information in order to enhance network visibility and secure network access for the IoT era. DPI can be shared through the Genians Cloud.
Identity
Distinct information
- The name of Device Platform consists of manufacturer, device name, model number (Integrated with the Common Platform Enumeration (CPE) dictionary)
- The actual picture of the device platforms
- The list of device fingerprinting sources
- Network connection type (Wired, Wireless)
- Released Date
Context
- Business Information
- Product end of life (EOL)
- Product end of support (EOS)
- Manufacturer business status
- Manufacturer location (Country)
- Manufacturer homepage
- Extended Information
- Linked to Product webpage
- Linked to Google search engine
Risk
- Technology Vulnerability
- Provide Common Vulnerabilities and Exposures (CVE)
- Report device platforms exposed to vulnerability issues in real time
- Alert and notification
- Business Vulnerability
- Report manufacturer/vendor going out of business or being acquired, which can introduce systems that cannot be upgraded or patched
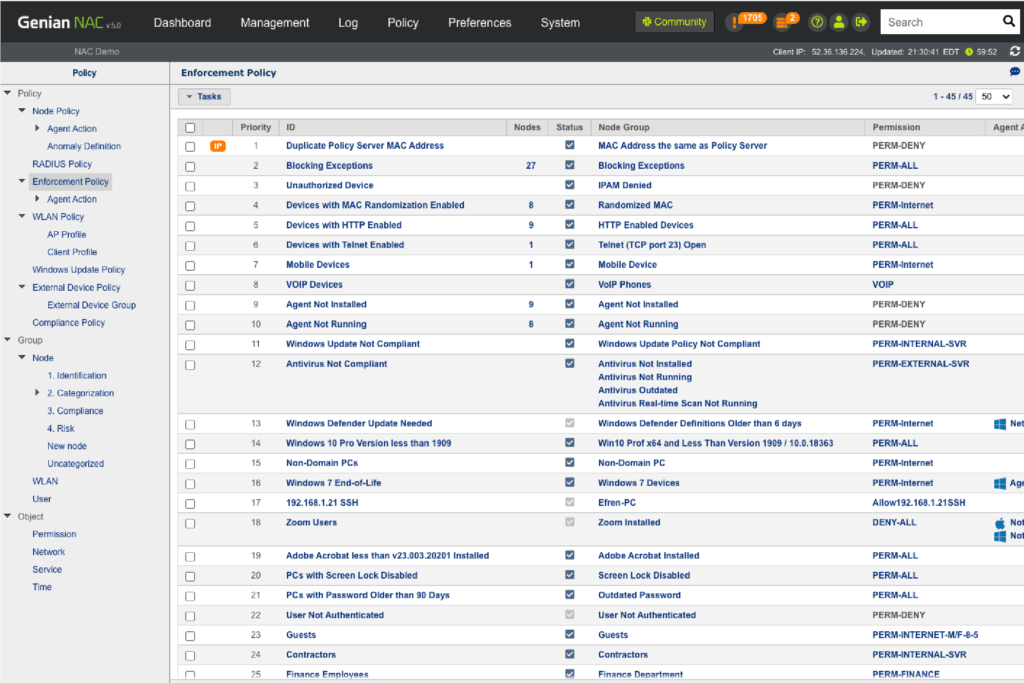
Network Access Control
Genian NAC leverages multiple techniques to enforce IT security policies dynamically using contextual information (What, Who, When, Where, How) to quarantine any non-compliant devices and remediate them to be compliant through automated processes.
Dynamic Acess Control
- Condition-based grouping (Over 500 predefined conditions)
- Policy assignment based on the status change of endpoint compliance
- End-to-end access control inside of LAN
Multi-layered Access Control
- 802.1x: Built-in RADIUS server
- DHCP: Built-in DHCP server
- Layer 2: ARP Enforcement (using Network Sensor)
- Layer 3: TCP reset (using Mirror/SPAN Sensor)
- Layer 3: Inline Enforcement (Dual-homed Gateway)
- Agent: NIC/Power Control, Alert Popup
- Integration: Firewall, Switch port shutdown (SNMP,Webhook)
Mobile, BYOD, Guest
In the hyper-connected world of the Internet of Things (IoT), organizations are grappling with implementing Bring Your Own Device (BYOD) initiatives to deal with the rapidly evolving and increasingly complex tsunami of mobile devices, from laptops and tablets to other smart ”Things”, such as phones, watches, cars and more. Genian NAC can provide flexible and secure network access, wherever you are located, and for whatever devices you bring to the network.
Onboarding Process
- Check user authentication and device compliance status
- Guide users to meet compliance (Self-service process)
- Provide role-based access control
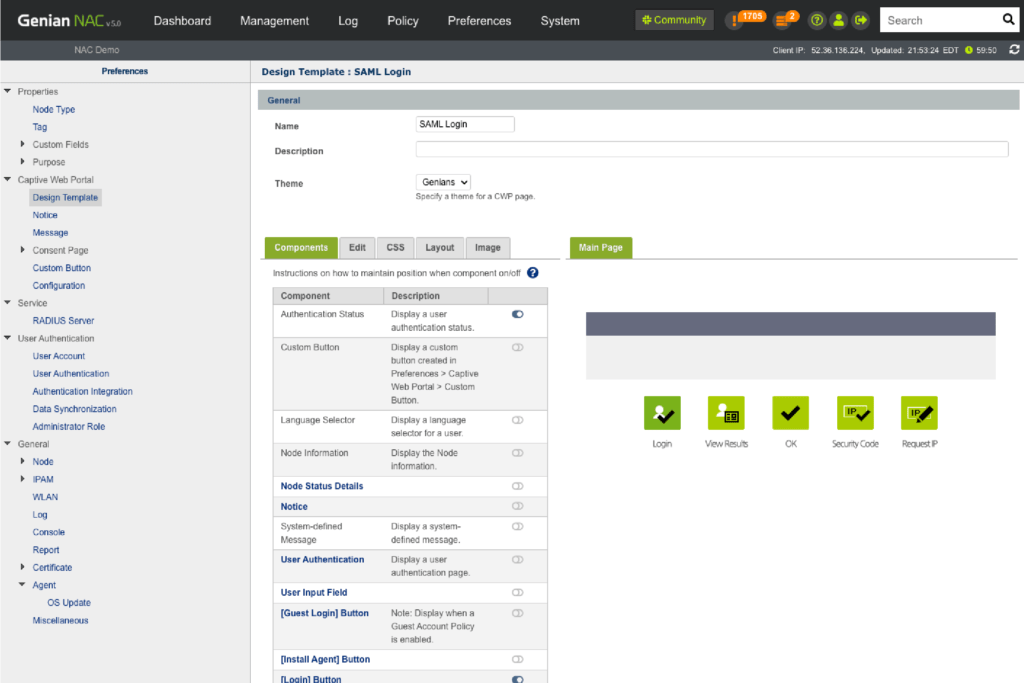
Secure Access Request
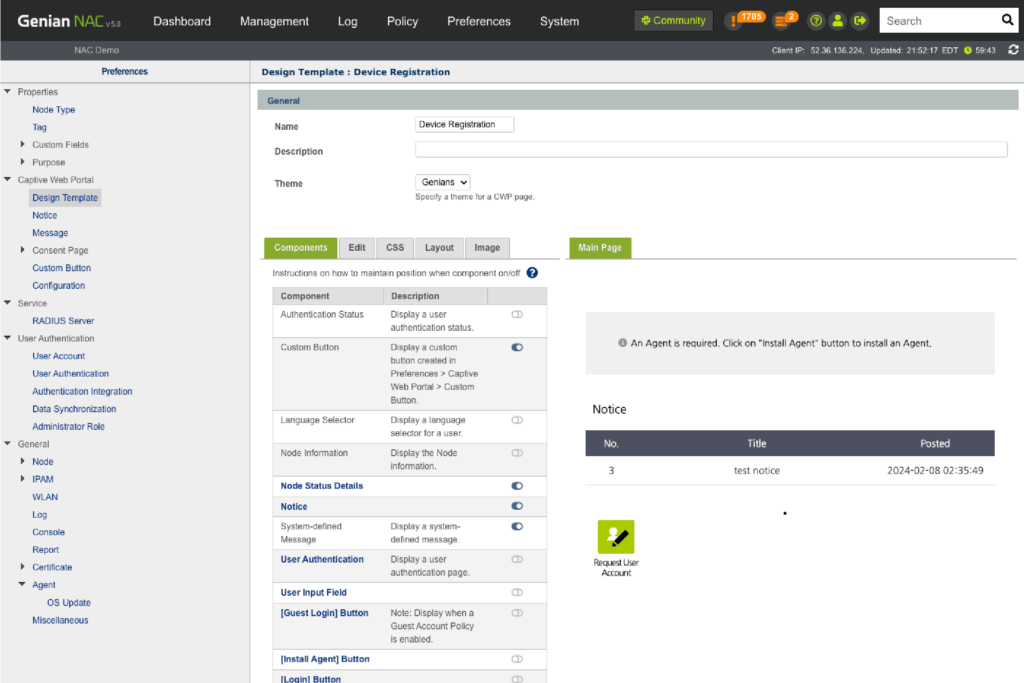
- Captive Web Portal service
- Built-in RADIUS server (802.1x)
- User authentication (AD, local DB, RDBMS, Google G-Suite)
- Request approval system (Device, IP, User, Peripherals)
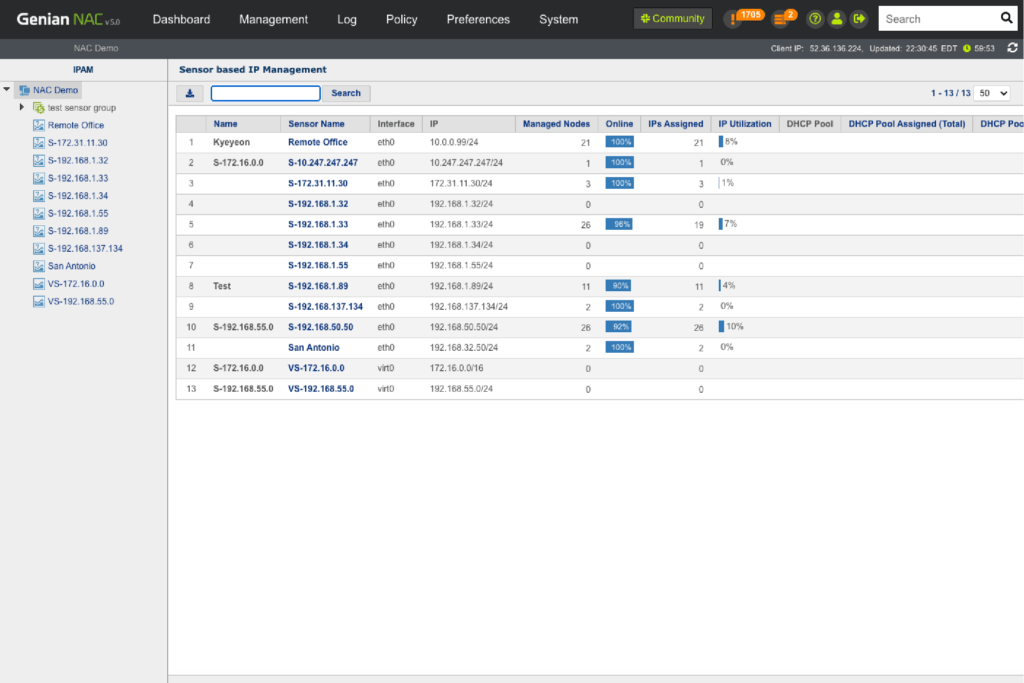
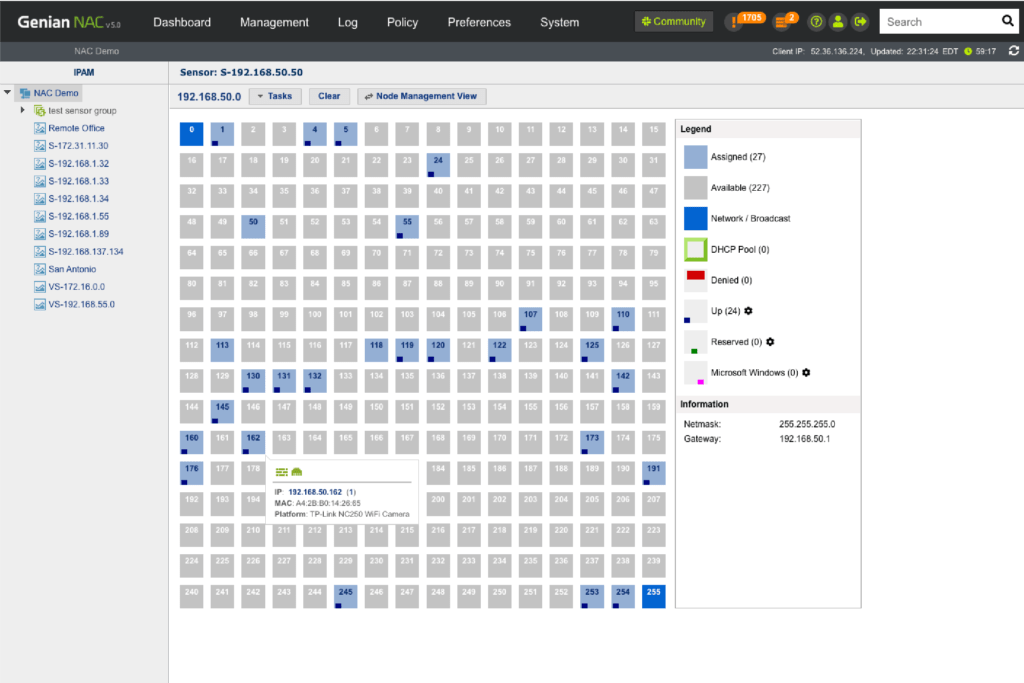
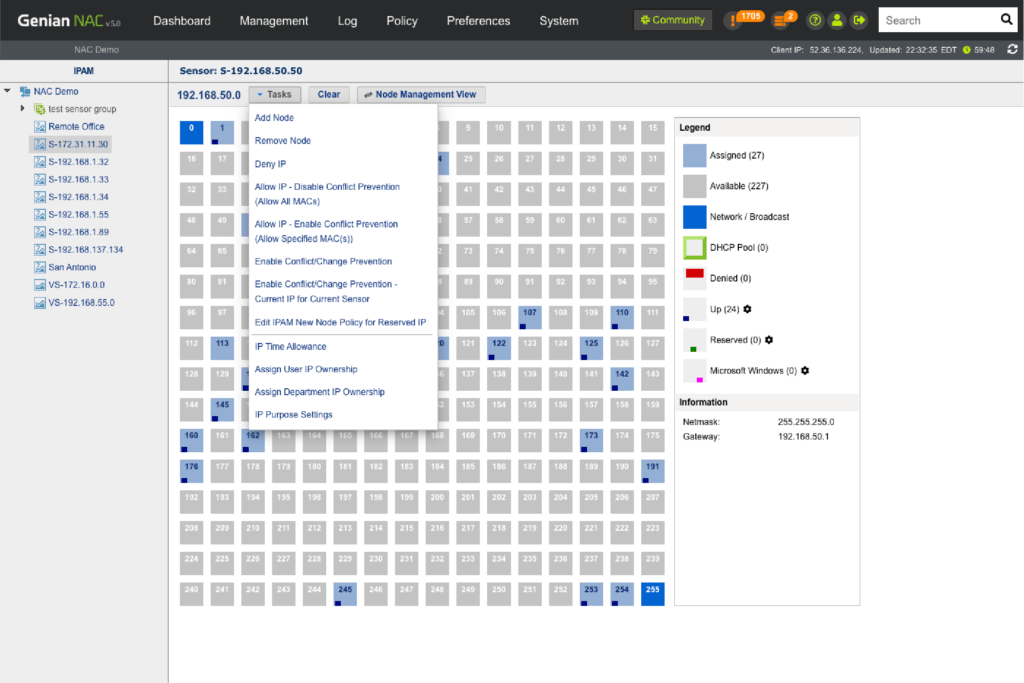
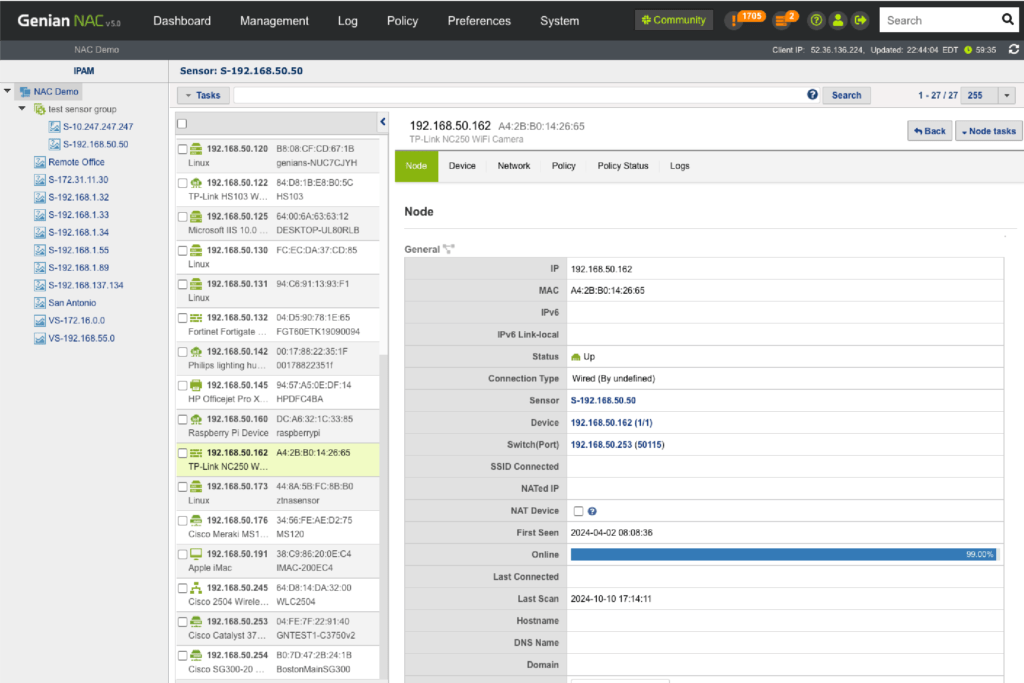
IP Address Management
Through our intuitive IP matrix interface (Class C Subnet mask), see how many IP addresses are being used and available, which IP’s are assigned via DHCP, which are reserved, and more.
Monitoring
- See the usage of IP address for each network segment
- Identify who/what device connecting to an IP address
Monitor the change of IP addresses
Comprehensive IP Management
- Built-in DHCP Server
- IP Address (Allow, Deny, Lease, Assign)
- IP Conflict / Change Prevention
- MAC/IP Cloning Detection
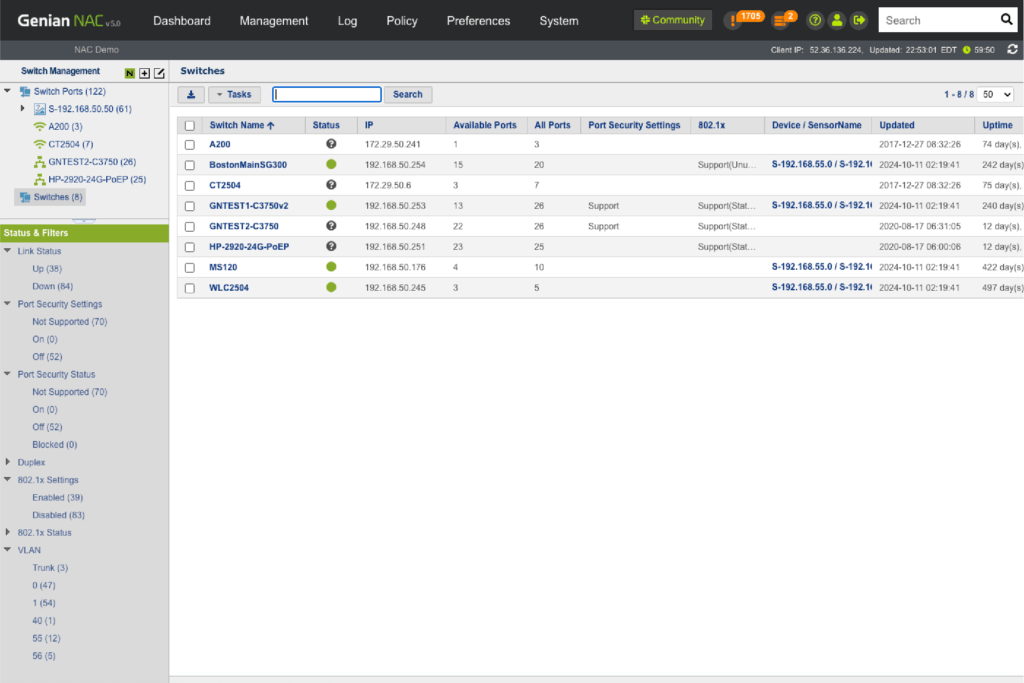
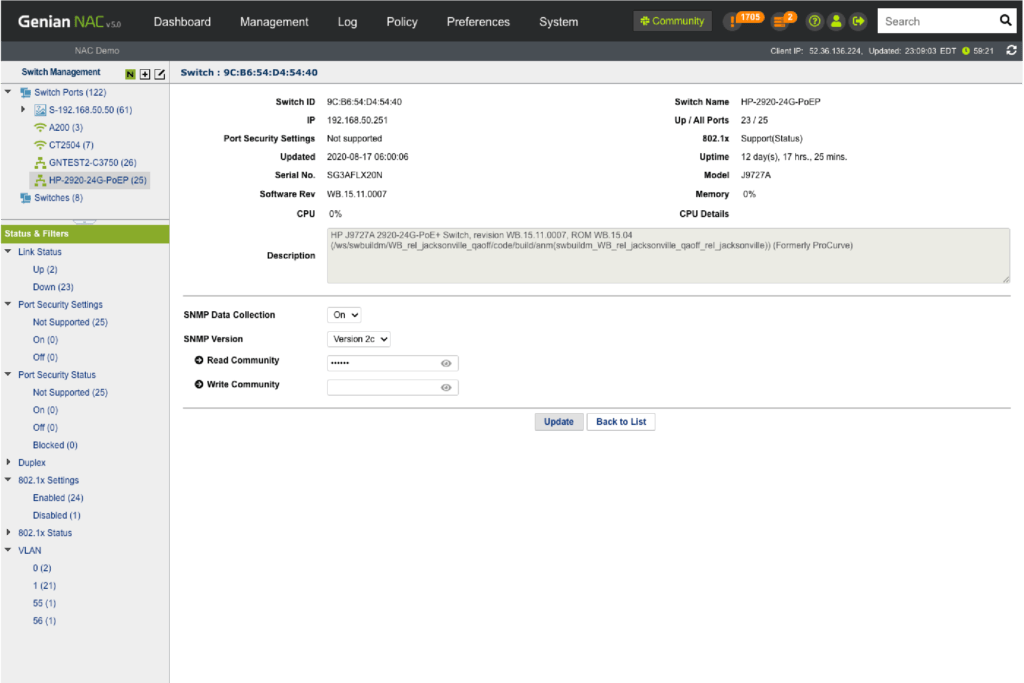
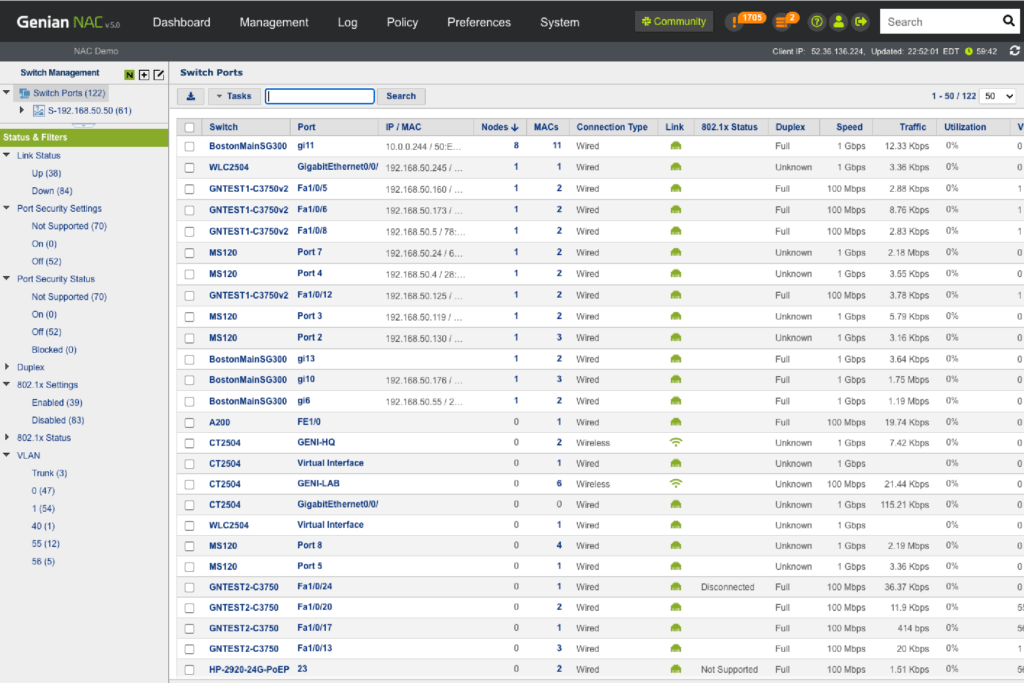
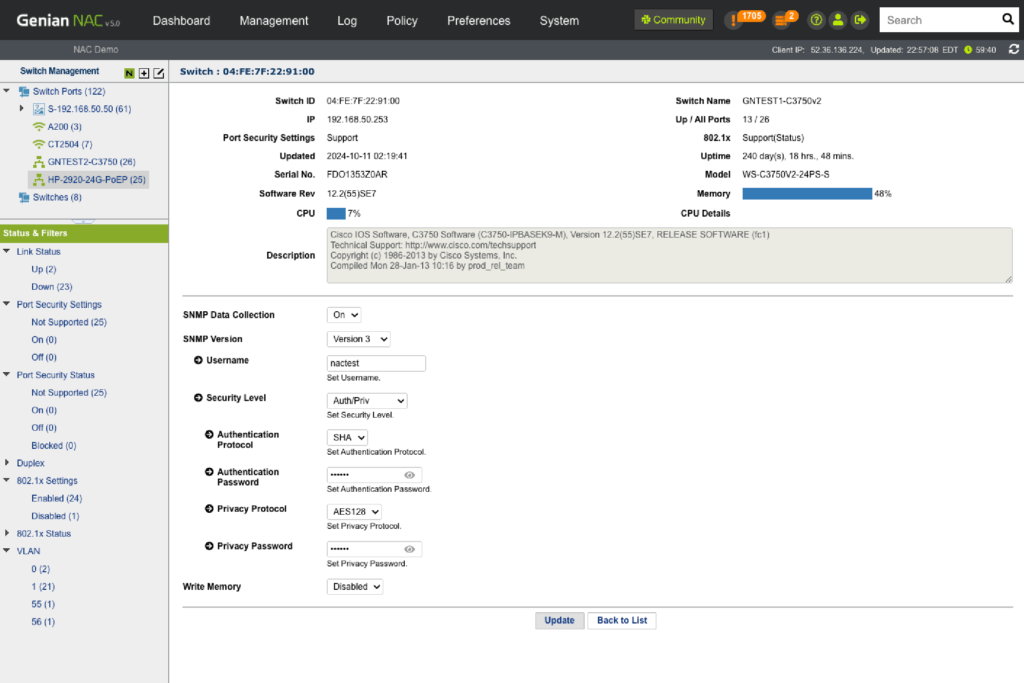
Switch Port Management
See how many devices are connected to specific ports, their connection status, port-level security, 802.1x information, traffic, utilization and more. Using 802.1x port-based access control, control any ports connected to non-compliant devices.
Monitoring
- Identify how many devices are connected to specific ports
- Check the authentication status of connected devices
- Monitor Switch port status (Up/down, Security, 802.1x, VLAN, etc.)
Port Management
- Switch and Port Description
- Administratively Down
- Discover Top 10 Switch Port Traffics
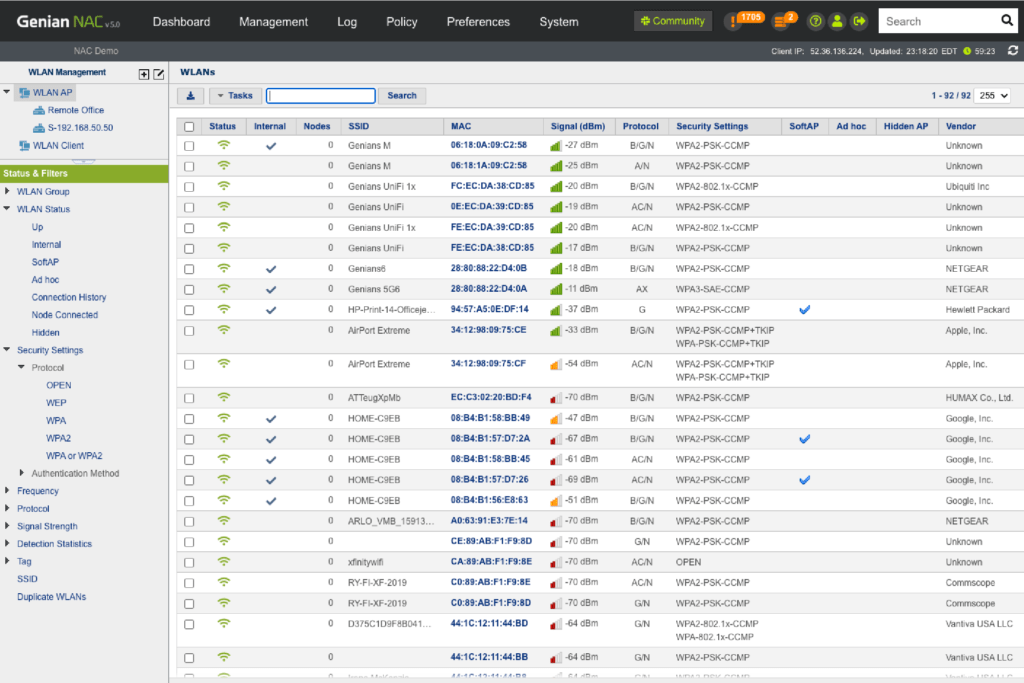
WLAN Security
Genians’ Network Sensor has the capability of scanning all SSIDs in your network and identifying who connects to which SSIDs, capturing not only your organization’s APs but also neighboring APs and controlling what is connecting to those APs. You can allow or deny Wifi-enabled devices accessing different SSIDs based on their policy compliance by groups, such as Authorized AP, Rogue AP, Misconfigured AP, Tethering device, and more.
WLAN Monitoring
- Detect SSIDs by Wireless Sensor or Agent
- Discover all connected wireless devices per SSIDs
- Discover where SSIDs are located
- Detect APs connected to corporate networks
WLAN Compliance
- Detect non-compliant wireless devices (APs, mobile devices)
- Detect rogue and misconfigured APs
- Detect hidden APs and softAPs
Wireless Connection Manager
- Manage wireless connection profile
- Disable SoftAP
- Provide a single-click wireless connection service
- Allow connections only to authorized APs
- 802.1x supplicant plugin (EAP-GTC)
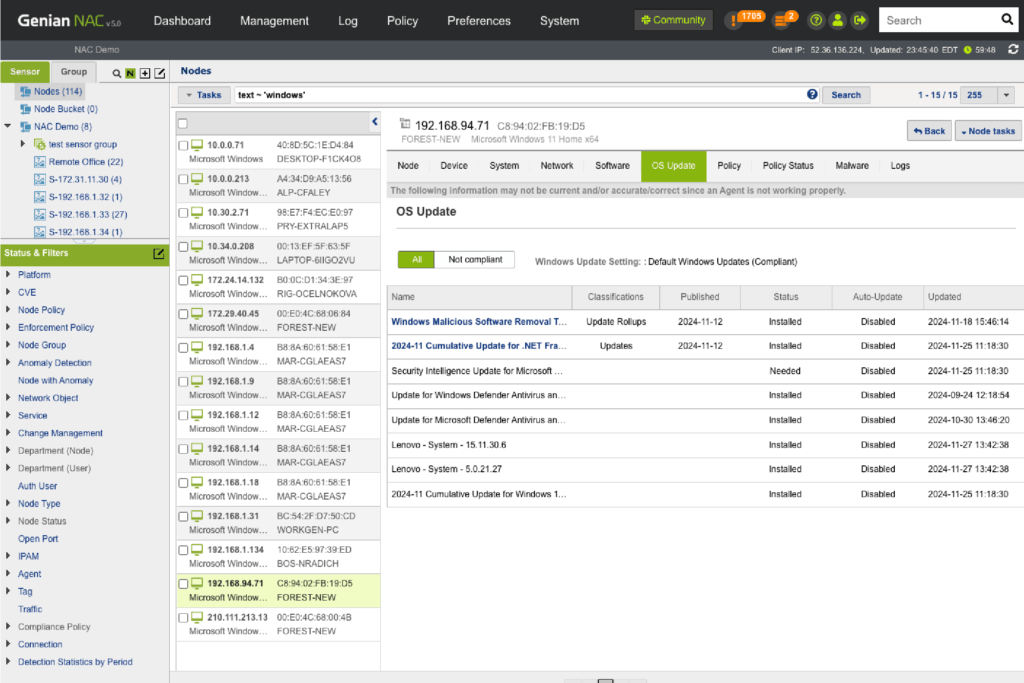
Endpoint Security
Manage all desktop configurations, applications, OS Updates, peripheral devices, wireless connections and more. Standardize the configuration of corporate-owned devices automatically and control them remotely.
- Change Computer Name
- Check Password Validation
- Collect System Information Using WMI
- Configure Windows Security Settings
- Control OS Updates (Works for the isolated network)
- Configure 802.1X Wired Authentication
- Profile Settings
- Control Antivirus Software Settings
- Control DNS
- Control External Devices (e.g. USB, Printer)
- Control Internet Explorer Security Settings
- Control Network Folder Sharing / Interface / Traffic
- Control Power Options, Screen Lock
- Provide Wireless Connection Manager (Zero configuration)
- Control WLAN
- Deploy Files
- Inspect TCP Connections
- Manage ARP Table
- Install / Remove software
- Run Scripts
- Terminate Processes
IT Security Automation
Genian NAC integrates a wide range of IT security and business solutions (Firewall, VPN, IDS/IPS, VM, MDM, SIEM, APT, DLP, CRM/ERP, etc.) to ensure unified policy enforcement. Genian NAC supports custom integration using Webhook, REST API, and Syslog.
Perimeter Security System (Next-gen Firewall)
- Give: IP-User information for user-aware policy
- Take: Receive Infected Endpoint IP or MAC then quarantine it
Threat Detection System (SIEM, ATP, VA, EDR)
- Give: IP information (user, history, platform.)
- Take: Receive Infected Endpoint IP or MAC then quarantine it
Enterprise Mobility Management
- Give: New device information
- Take: Block mobile devices if EMM agent is not installed
Critical Security Controls (CIS) for Effective Cyber Defense
Cybersecurity compliance and risk management are distinct priorities—but achieving strong cyber defense requires both to work hand in hand. Genian NAC empowers this balance by directly supporting the foundational Controls defined by the Critical Security Controls (CIS).
The CIS Controls are globally recognized best practices designed to protect IT systems and data from modern threats. Genian NAC helps organizations implement the first six foundational CIS Controls to strengthen security and meet compliance goals effectively.
| CIS BASIC Controls | PCI DSS | HIPAA | ISO 27002 | Cloud Security Alliance | NIST | NSA | NERC CIP | Saudi AMA |
|---|---|---|---|---|---|---|---|---|
| 1. Inventory and Control of Hardware Assets | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| 2. Inventory and Control of Software Assets | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| 3. Continuous Vulnerability Management | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| 4. Controlled Use of Administrative Privileges | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| 5. Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations and Servers | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| 6. Maintenance, Monitoring and Analysis of Audit Logs | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
Components
Seamless Security. Zero Disruption
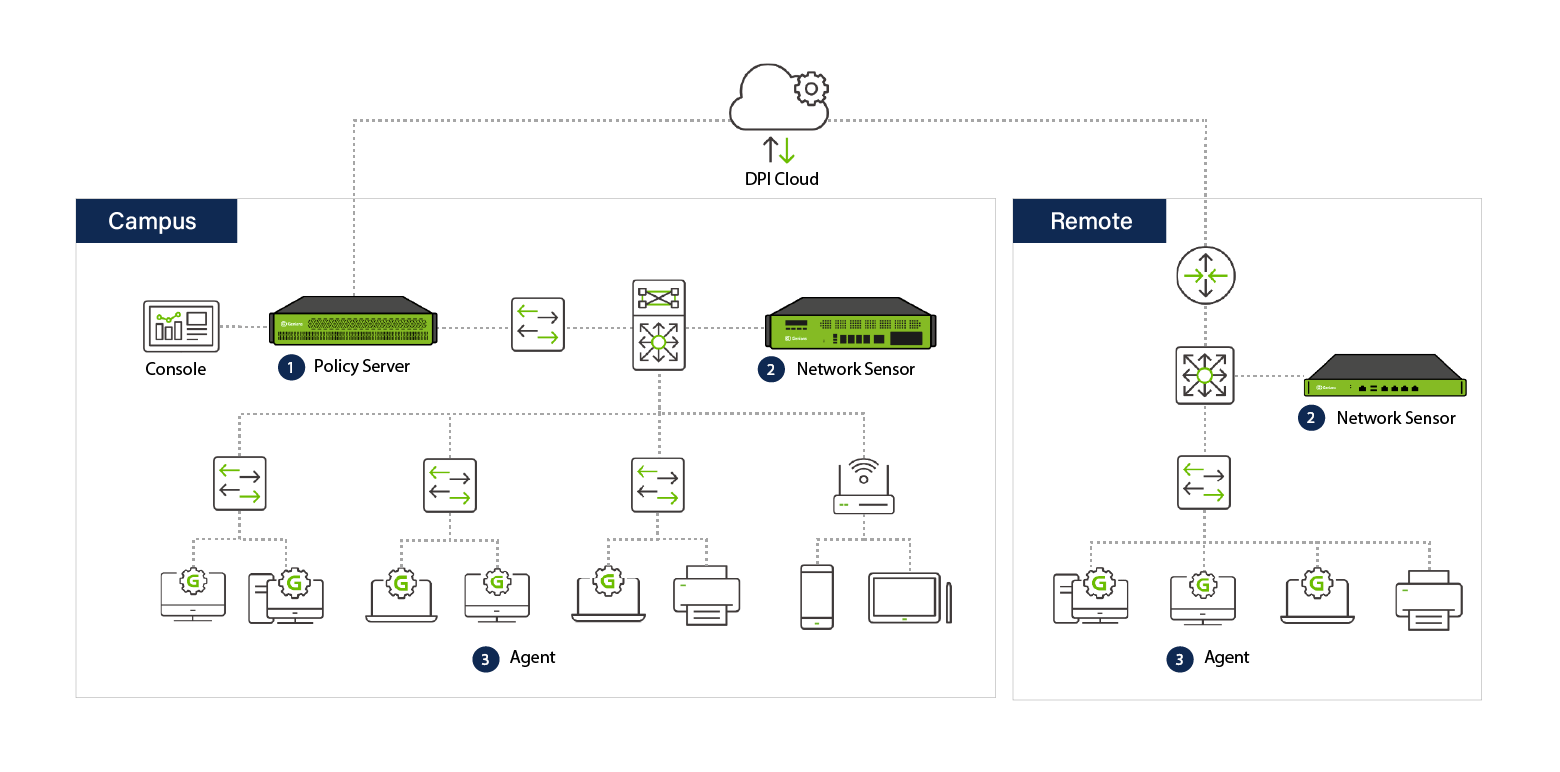
DPI Cloud
Review and refine device platform information via the cloud and deliver the most accurate, up-to-date device platform information to Policy Server on a weekly basis.
Policy Server
Establish security policies based on Node info collected by Network Sensors and Agents.
- Distribute established policies to Network Sensors and Agents
- Communicate with Network Sensors and Agents to secure access control
- Integrate with user database and third-party security solutions
Network Sensor
Collect Node Information from network and enforce access control polices.
- Apply (or enforce) established policies from Policy Server to targeted Node (or Node groups)
- Detect all SSIDs by listening wifi signals
- Identify who is accessing valid (enterprise-owned) APs, neighbor APs, or rogue APs
- Support 802.1q Trunk Port
Agent (Optional)
Control endpoint system (all installed hardware and software) in detail
- Execute policy enforcement as well as management tasks through the use of Plugins.
- Operate as a Wireless Sensor to provide wider and more in-depth coverage to detect any possible Wifi activities such as Ad-hoc mode, SoftAP, and Tethering.
Get Started
You Pick, We Deliver.
Genian NAC delivers essential cybersecurity features in a single, cost-effective solution.
Choose from three flexible deployment options based on what best fits your business needs.

Cloud NAC
No credit card or phone call required.
Pricing