Compliant Velocity
Always-on security that adapts when regulation changes
Genians delivers a security platform that keeps compliance, access, and endpoint control in sync so when regulation or risk changes, your environment adapts in real time across users, devices, and networks.
ALWAYS-ON COMPLIANCE
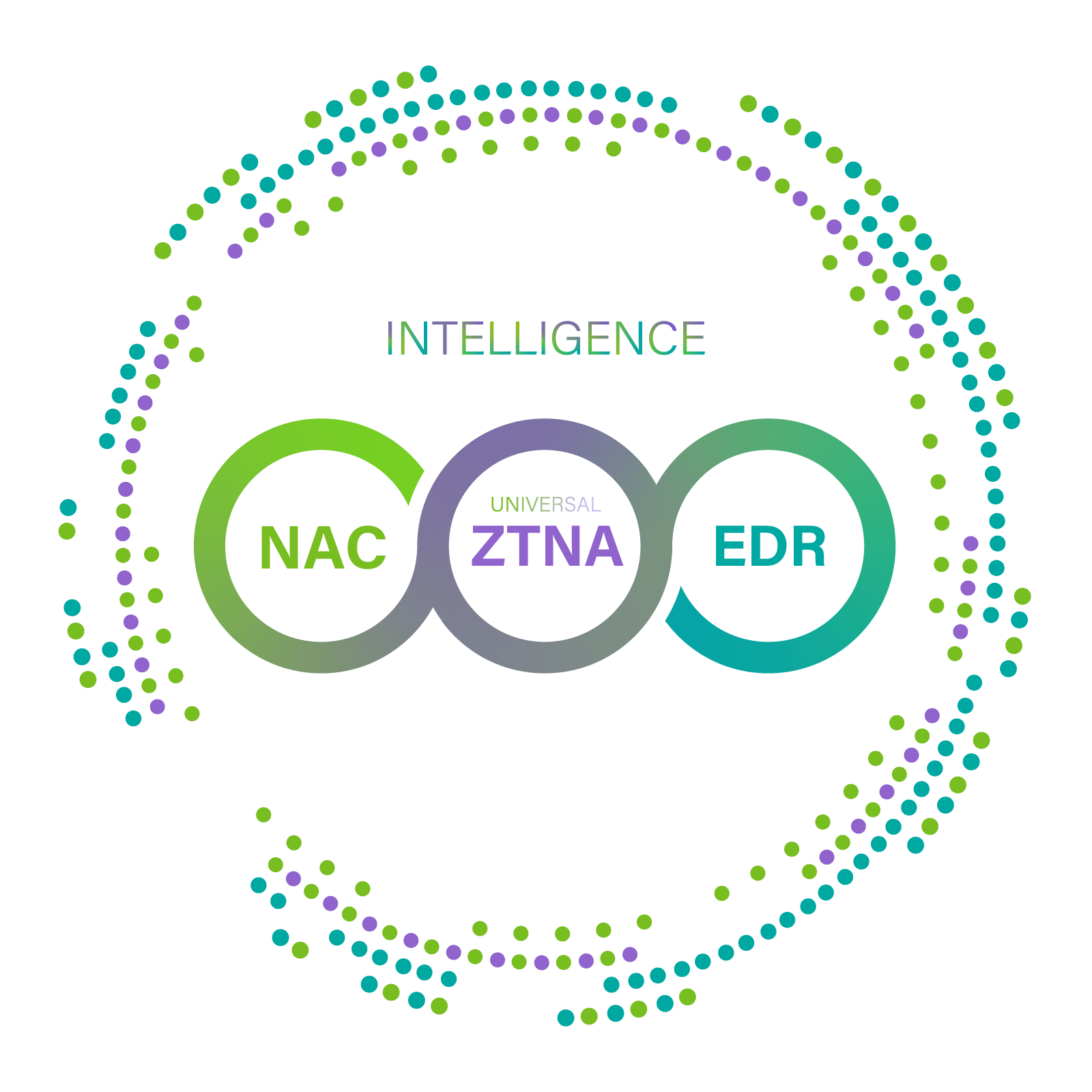
How Compliant Velocity Becomes Action
Genians turns real-time endpoint and network intelligence into continuous enforcement across NAC, ZTNA, and endpoint controls. NAC, ZTNA, and endpoint controls operate as coordinated execution planes, sharing device, identity, and threat context powered by a single intelligence layer so that access, policy, and protection adjust instantly as risk and regulation change.
What You Need
GENIANS
Proven by Numbers
Consistent Profitability
Years
2024 Annual Revenue
34
M
Happy Customers
Over
5000
Network Sensors Deployed
Over
100
K
In Genians We Trust
Where Trust Meets Results






Empowering 5,000+ Companies – From SMEs to Fortune 500s.
Genians in Action
From Challenge to Success
FAQ
Clear Answers to Common Questions
Q. What do “Zero Network Changes” and “Zero Integration” mean when using Genians’ solutions?
Genians’ Network Sensing technology provides complete network visibility and access control without requiring changes to your existing network infrastructure or relying on integration with third-party systems such as Switches, Wireless Controllers, etc. This streamlined approach ensures effortless deployment and enhanced security.
Q. Genians offers NAC, ZTNA, and EDR solutions. Are they provided through a single platform?
No, each solution is available individually, but they can also be seamlessly integrated to work together, providing enhanced security and management capabilities.
Q. If I want to manage my Campus Network while using ZTNA, do I need to purchase NAC separately?
No, unlike other ZTNA solutions, Genian ZTNA already includes NAC functionality. By using Genian ZTNA, you can seamlessly manage Campus Networks, Remote Access, Applications, and Cloud security through a unified platform.
Q. How scalable are Genians’ solutions for various network environments, including legacy, hybrid, and evolving networks?
Genians’ solutions are highly scalable and designed to support all types of network environments. With flexible deployment options such as On-Premise, Cloud-Managed, and As-a-Service models, you can seamlessly expand and secure your network without disruption, regardless of its complexity.