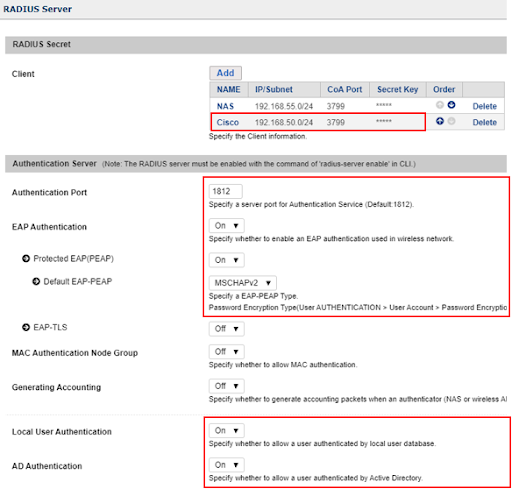
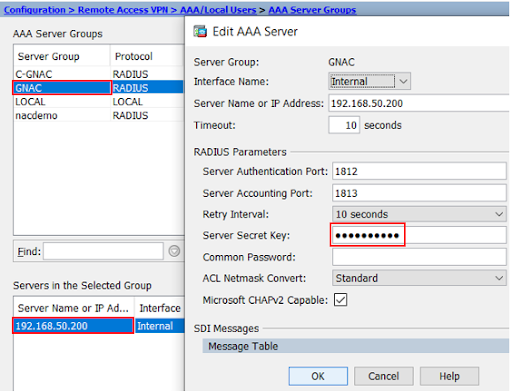
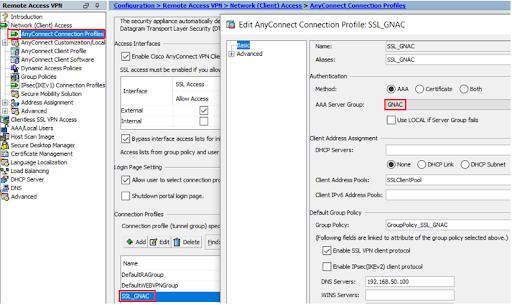
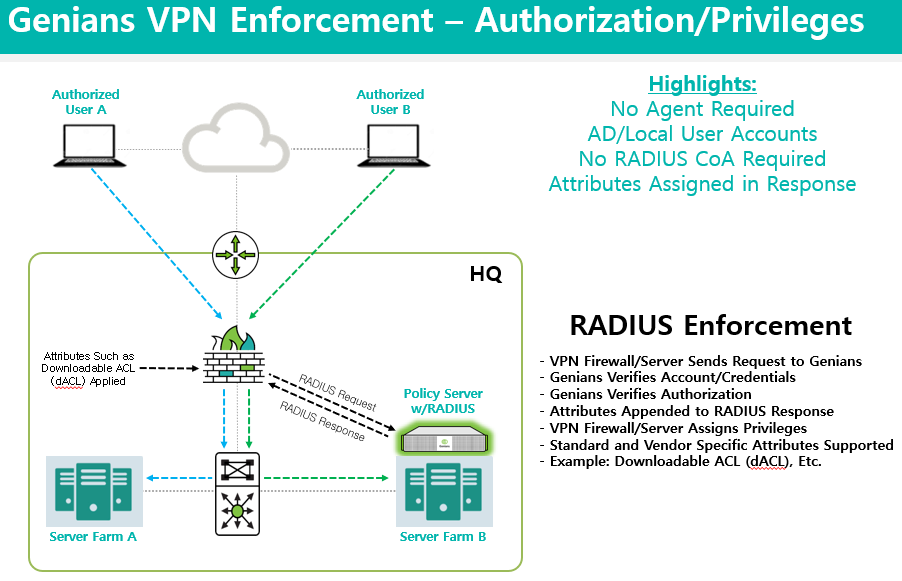
The Genian NAC Built-In RADIUS Server is capable of performing Authentication, Authorization and Accounting functions for Enterprise and SMB/SME networks. This capability not only applies to On-Perm users and devices, but can be extended to remote VPN connections as well by integrating with Firewalls and VPN Concentrators/Servers.
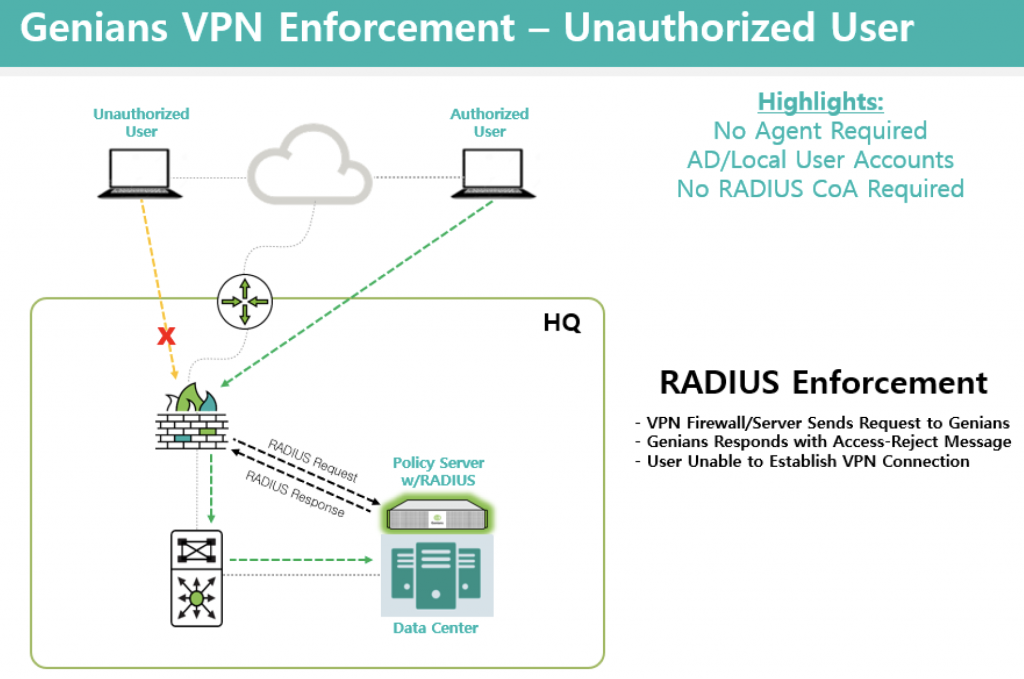
In this configuration example, RADIUS AAA integration with VPN is leveraged to authenticate users, deny access to users with valid credentials but not authorized to use the VPN and assign privileges on the internal network to authorized VPN users. Unauthorized devices will also be blocked using the Global Mirror option. This ensures that no person or device without expressed permission to utilize the VPN can connect and also ensures lease privileged access when connected. Authorized Devices will also be forced to comply with Endpoint Security Policies.
Global Config (Genian NAC, Cisco ASA)
RADIUS Server Configuration Example
Cisco ASA RADIUS Configuration Example
Cisco ASA Client VPN Configuration Example
Use Case 1: Controlling Remote VPN Users
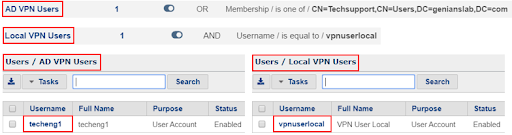
User Group Configuration Example
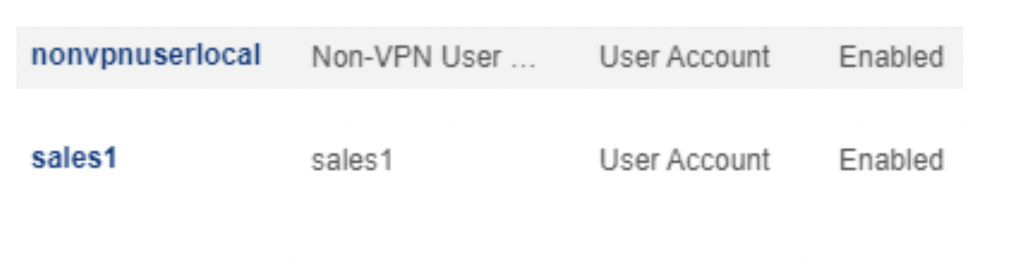
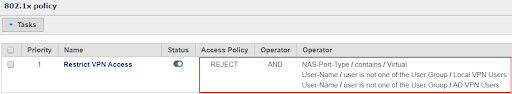
Defining User Groups that will include users authorized to connect via VPN is the first step. In this example, we have created both a Local User Group and an Active Directory User Group to demonstrate how VPN can be permitted or denied by User Group regardless of whether it is a locally defined user in the Genian NAC database or a user defined in Active Directory. Once tied to the correct policy, the group criteria can be matched on, ensuring only VPN authorized users will be able to successfully authenticate.
802.1X Policy Configuration Example
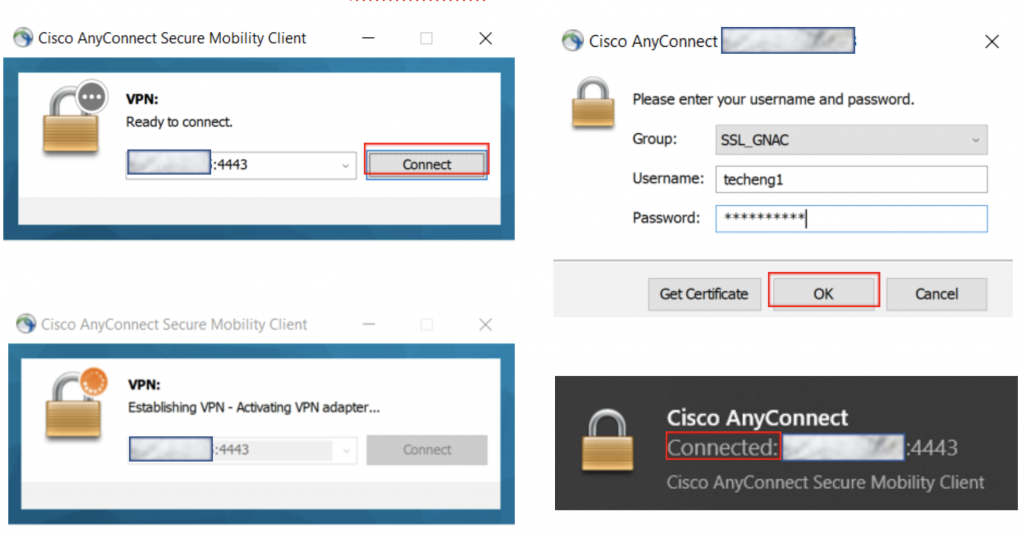
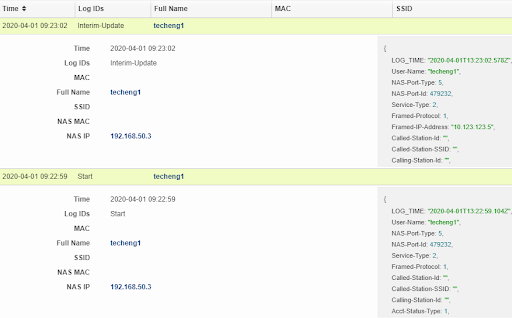
Authorized User Test
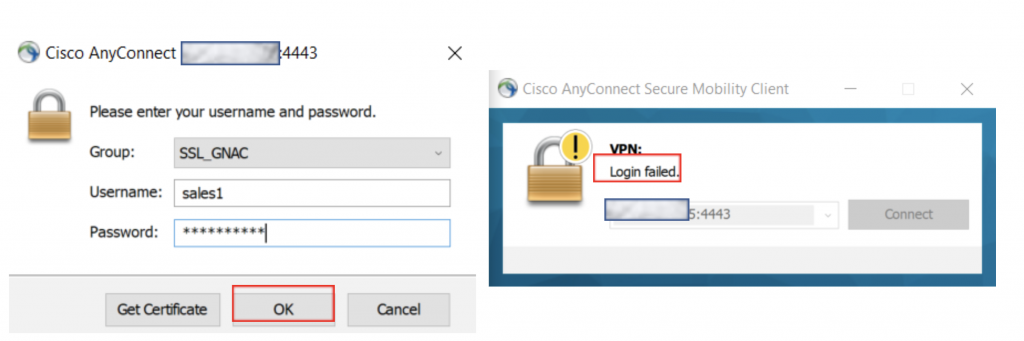
Unauthorized User Test
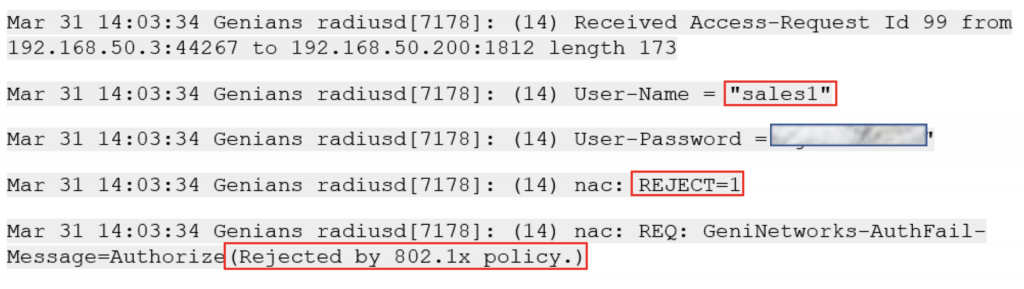
To confirm that unauthorized users are not able to connect, we will attempt to connect with with an unauthorized Active Directory user account “sales1”. The AnyConnect client should respond with “Login failed”. The same results should be observed if testing with an unauthorized Local account such as “nonvpnuserlocal”.
Use Case 2: Authorization (Privilege/Access Assignment)
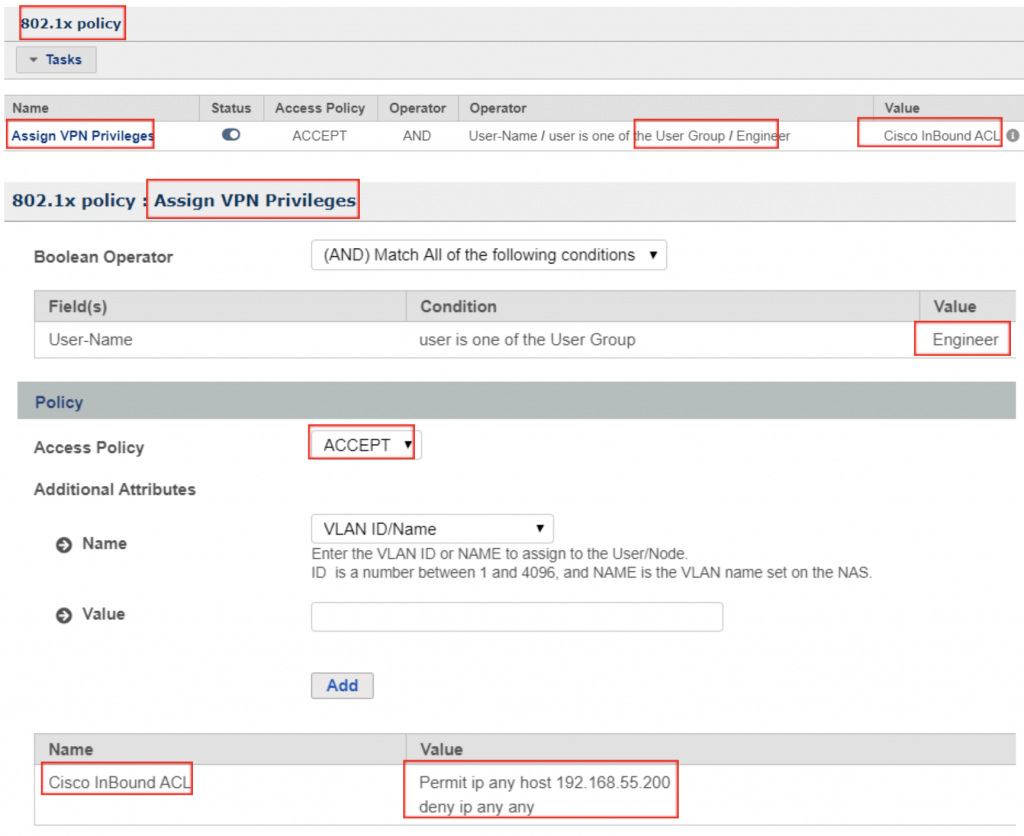
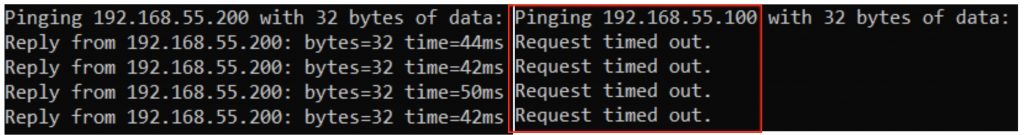
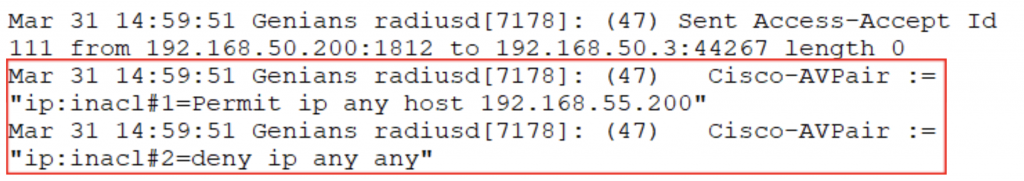
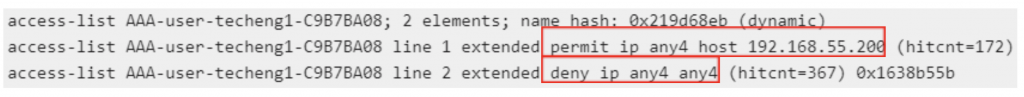
Users that are authorized to connect via VPN should be assigned the least amount of privileges or access required. This can be accomplished through RADIUS Authorization. RADIUS attributes such as Downloadable ACLs (dACLs) can be applied based on various conditions such as Identity or Group. In the example below, any user account that is a member of this particular “Engineer” Group will only be allowed access so a single IP on the network (perhaps a server or network device for example). After successful Authentication, Authorization takes place and the dACL is applied to the user’s VPN session, restricting access based on the rule.
802.1X Policy Configuration Example
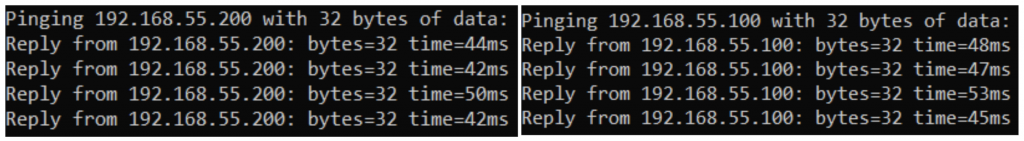
Authorization Test
Use Case 3: Controlling Remote VPN Devices

With only authorized users allowed to connect and with the appropriate privileges assigned to those users, the final use case example is how to block unauthorized devices from accessing internal network resources. This is accomplished by utilizing the Genian NAC Global Mirror option.
Since MAC address information is not included with VPN RADIUS Accounting, the Global Mirror option is utilized for Enforcement instead of RADIUS. Corporate/Organization issued devices will be deployed with the Genian NAC Agent. Any device that does not have an Agent installed will be denied access to internal network resources.
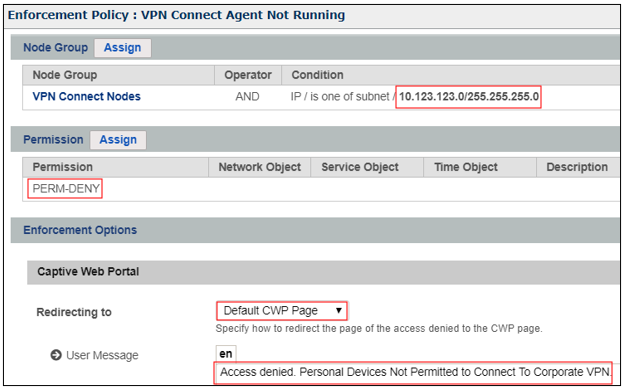
Enforcement Policy Configuration Example
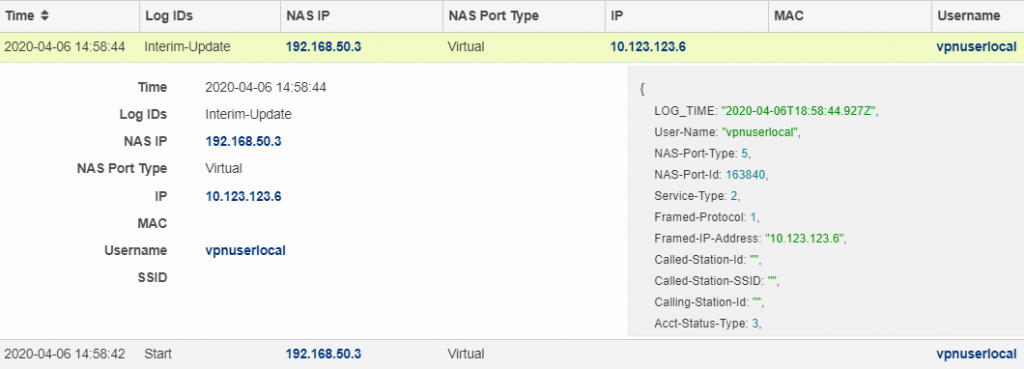
Unauthorized Device Test
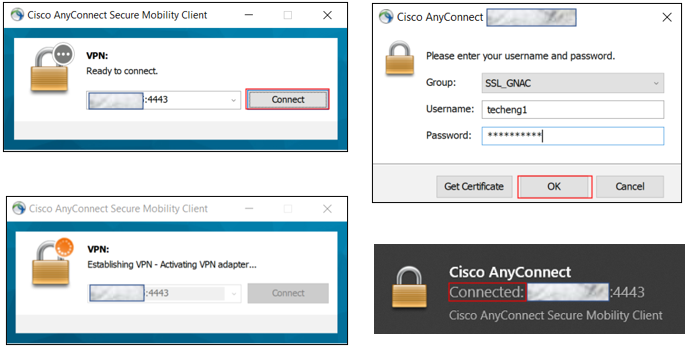
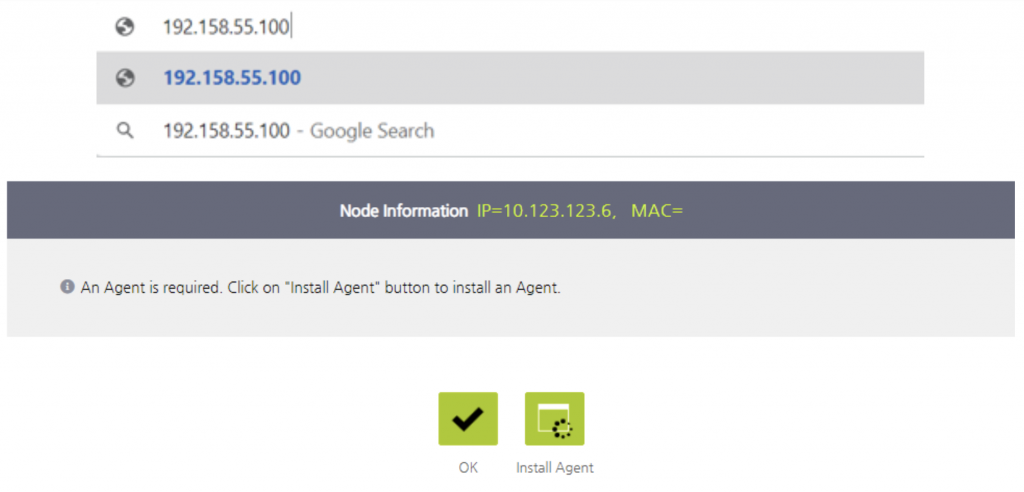
The example below will show a user connecting with valid credentials, but the connection is being initiated from a device with no Agent installed.
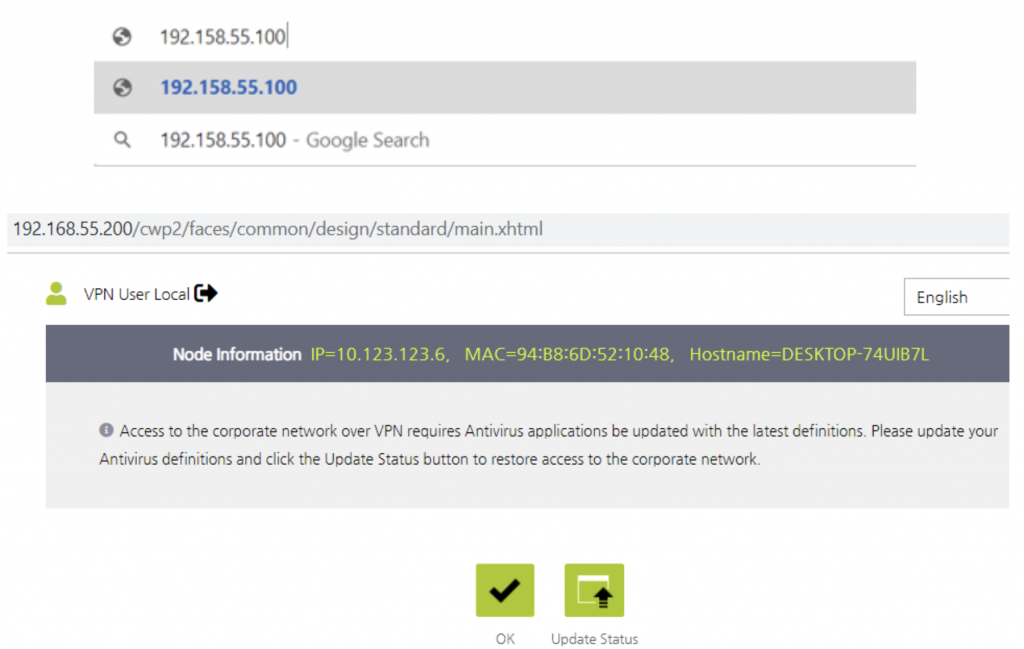
However, if the user attempts to navigate to an internal resource on the network, the session will be redirected and a Captive Web Portal message will be displayed.
The message above can be customized including removing the Install Agent option if the desire is just to display a message that advises non-Corporate devices are not permitted to connect through VPN. Their key is to customize the message as much as possible to either allow the user to connect if personal devices with Agents are permitted, or to ensure the appropriate security policy is displayed as well as Help Desk contact information if needed.
Use Case 4: Endpoint Security for VPN Devices
Policy Configuration Example
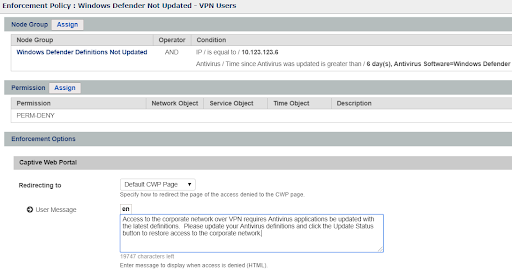
In the example below, the VPN IP Pool subnet is listed as a condition for the policy. When operating in Global Mirror mode, any Windows VPN connected node that does not have updated definitions for Windows Defender will be denied access. An optional Captive Web Portal message may also be displayed.
Policy Test:
This is only one example of an Endpoint Security policy available. For the complete list of Agent plug-ins and detailed explanations of each, see the Agent documentation page.